Global consent
The following countries require mobile network operator (MNO) consent to integrate Verified Users. Please contact your Prove representative to discuss requirements.- Canada
Prerequisites
- Sandbox credentials: Ensure you have Prove Sandbox credentials from the Developer Portal. To access Sandbox credentials, follow the steps outlined on the Authentication page. To access the Prove API, use your OAuth 2.0 client ID and client secret. Load these from environment variables or another method:
Token ExpirationThe OAuth token expires after 60 minutes, requiring you to get another token.
- Server-side SDK: Install the server-side SDK of your choice by running a command in your terminal, or by using a dependency management tool specific to your project.
- Client-side SDK: Install the client-side SDK of your choice by running a command in your terminal, or by using a dependency management tool specific to your project.
To integrate Verified Users with Possession, you must use the client-side SDK.
- Web SDK
- Android SDK
- iOS SDK
Implement Prove Verified Users
- With Possession
- Without Possession
1
Prompt Customer
Create or update your first screen to prompt the customer for phone number, first name, and last name.
2
Determine Type of Flow
- Web SDK
- Android SDK
- iOS SDK
You can determine if the customer is on a mobile or desktop browser using this example. If the
isMobile is true, set mobile as the possessionType for the Start() function on the server, otherwise you can set desktop:3
Call the Verify Endpoint
On the back end, you’ll start a Prove flow with a call to the The function returns the following fields:
Verify() function. This function takes these required parameters:-
possessionType: eitherdesktopormobileto describe which type of device the customer is starting their flow on. -
phoneNumber: the phone number of the customer. -
firstName: the first name of the customer. -
lastName: the last name of the customer. -
finalTargetURL: required whenpossessionType=desktop. This should be a URL you maintain. Once the customer clicks the Instant Link, they will be redirected to this URL. It should instruct the customer to continue the workflow. Maximum length is 128 characters.
-
smsMessage: a field to customize the message body sent in the Instant Link or OTP SMS message. Otherwise, you can use Prove defaults. -
clientCustomerId: a client-generated unique ID for a specific customer. You can link calls related to the same customer, across different requests or sessions. The client defines the format of this ID. -
clientRequestId: a client-generated unique ID for a specific request. You can identify specific requests using this field. You determine the format of this ID. -
allowOTPRetry: set totrueto allow the customer to re-enter the OTP up to three times. Defaults tofalse.For OTP retries, make sure to implement client SDK changes in the next step.
-
authToken: send this to your client-side code through theAuthenticate()function - it’s a JSON Web Token (JWT) tied to the current flow and used for the possession checks. It expires after 15 minutes. -
correlationId: save this in your current session, then pass it in toVerifyStatus()of the same flow. The correlation ID ties together different system calls for the same Prove flow. It can aids in troubleshooting. The session expires in 15 minutes from when the correlation ID returns from theVerify()call. -
possessionResult: will returnpendingsince the possession check needs to complete first. -
verifyResult:pendingsince the verification check needs to complete first. -
success: the result of the combination ofverifyResultandpossessionResult. A result ofpendingis returned until the Verify and Possession checks are completed.
authToken in a response to the front end.4
Authenticate
Once you have the To set the One-Time Password (OTP) handler, To set the Instant Link handler, In the desktop flow, a WebSocket opens for three minutes on the desktop browser while waiting for the customer to select the link in the text message. Once clicked, the WebSocket closes and the
authToken, build the authenticator for both the mobile and desktop flows.- Web SDK
- Android SDK
- iOS SDK
Configure OTP
To use the Resend/Retry/Phone Change features, you need to install the Web SDK version 2.15.1 or later.
withOtpFallback(startStep: OtpStartStep | OtpStartStepFn, finishStep: OtpFinishStep | OtpFinishStepFn), requires implementing the OtpStartStep and OtpFinishStep. When returning the phone number in the functions, ensure you return an object with the field phoneNumber to the resolve() function.The OTP session has a two minute timeout from when it’s sent through Short Message Service (SMS) to when the customer can enter in the OTP.- Default
- Prompt for Phone Number
- Resend
- Retry OTP
- Phone Number Change
Follow these instructions if you are implementing OTP and you are passing in the phone number on the Call the
/v3/start endpoint. In this case, you’ve already prompted for a phone number so you don’t need to prompt for it in the client SDK.Since you passed the phone number in the Start() function, call resolve(null) to communicate to the SDK you have the customer’s agreement to deliver the SMS message. Ensure you return an object to resolve() function.reject('some error message') method to communicate to the SDK any issues while trying to obtain the phone number or the OTP. Report an error if the customer cancels the SMS transaction or presses the back button to leave the screen.In the finish step, call the resolve(result: OtpFinishResult) method to return the collected OTP value in which result variable has OnSuccess value for OtpFinishResultType and the OTP value wrapped in OtpFinishInput.Configure Instant Link
To use the Resend/Retry/Phone Change features, you need to install the Web SDK version 2.15.1 or later.
withInstantLinkFallback(startStep: InstantLinkStartStep | InstantLinkStartStepFn, retryStep?: InstantLinkRetryStep | InstantLinkRetryStepFn) requires implementing the InstantLinkStartStep interface and optionally the InstantLinkRetryStep interface if you wish for advanced capabilities. When returning the phone number in the functions, ensure you return an object with the field phoneNumber to the resolve() function.The Instant Link session has a three minute timeout from when it’s sent through Short Message Service (SMS) to when the customer can click the received link.- Default
- Prompt for Phone Number
- Resend
- Phone Number Change
Follow these instructions if you are implementing Instant Link and you are passing in the phone number on the
/v3/start endpoint. In this case, you’ve already prompted for a phone number so you don’t need to prompt for it in the client SDK.Since you passed the phone number in the Start() function, call resolve(null) to communicate to the SDK you have the customer’s agreement to deliver the SMS message. Ensure you return an object to resolve() function.AuthFinishStep function finishes.If you’re using Content Security Policy headers, ensure you allow
wss: device.uat.prove-auth.proveapis.com and wss: device.prove-auth.proveapis.com.5
Verify Mobile Number
In the
AuthFinishStep, you’ll specify a function to call once the possession checks complete on the mobile phone. This endpoint on your back end server calls the VerifyStatus() function to validate the phone number. The AuthFinishStep then completes.- Web SDK
- Android SDK
- iOS SDK
6
Validate Possession and Ownership of Mobile Phone
Once the possession checks finish on the mobile device, the finish handler on the client-side SDK executes. You then make a request to your server such as The function returns the following fields:
POST /verify-status to make the next call in the flow to the VerifyStatus() function.This function requires the Correlation ID which is returned by the Verify() function.-
success: The result of the combination of Verify Result and Possession Result. Possible values aretrueorfalse. -
possessionResult: eithersuccessif the possession check was successful orfailedif it failed. -
verifyResult: eithersuccessif the verification was successful orfailedif it failed, ornot_applicableif possession failed.
Webhook notifications
Webhook notifications are only available for US-based phone numbers.
1
Access the Portal
Login to the Portal.
2
Find Your Project
Navigate to your Verified Users project.
3
Configure Webhook
Select the Configure button from the Configure tab next to the Sandbox webhook. Enter the URL of your webhook endpoint and select Save and Test Webhook. This will save your configuration and send a test webhook to the URL you provided.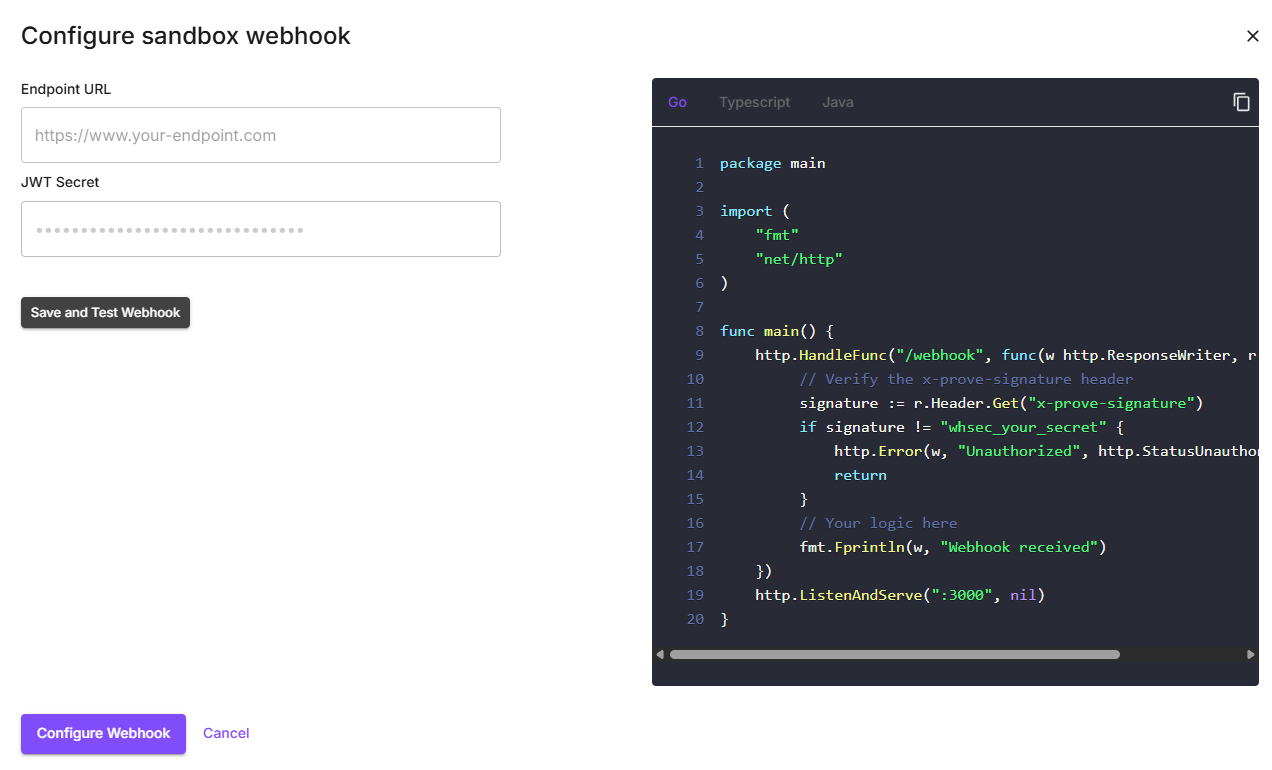

If you would like a sample URL to test, you can use Webhook.site to generate a unique URL for testing.
4
Authenticate Webhook
The webhook URL must be authenticated using Prove’s JWT secret. The JWT is a synchronous JWT using HS256 (synchronous algorithm).This secret is used to sign the JWT token that Prove sends with the webhook notifications. Open the webhook configuration and add the appropriate code snippet to your server-side implementation, replacing
whsec_your_secret with the secret provided by the Portal.The secret value is autogenerated when the appropriate URL is entered and you select Save and Test Webhook or Configure Webhook.
5
Parse the Webhook Payload
The following snippet shows an example of each type of change event you could receive from Prove. Each notification will come as an array of event objects.
Example Payload
Field Definitions
Field Definitions
A unique event ID to reference if you need support.
A description of the event.
The event type.
The time the event is sent.
The client customer ID if one is associated with the identity.
The unique ID associated with the identity.
If you would like to stop receiving notifications for an identity, make a request to the /deactivate endpoint. This will stop all notifications for that identity.
6
Access Production
Once you have successfully tested the webhook and finished your implementation, configure and test your production webhook URL. This will allow you to receive notifications for live events.
Why Am I Not Receiving Notifications?
- Prove will not send retroactive notifications that occur before the webhook is configured.
- An identity that has been deactivated will not receive any further notifications.
-
By nature of each change event, an event triggering for an
identityIdwill result in no further notifications for that identity. In the event your customer provides an updated phone number, we’d recommend initiating a new verification with the updated identity information. If verification is successful, Prove will monitor the updated phone number.
Test your Prove implementation
Next, reference the Sandbox test scenarios to test users and simulate different behaviors encountered in production.Production LaunchTo launch in Production, please contact your Prove representative.

